DIGITAL LIFE
 Malware Agent Smith has infected more than 25 million Android devices
Malware Agent Smith has infected more than 25 million Android devices
Researchers at digital security firm Check Point Research have discovered quite unusual Android malware that is capable of infecting other apps and forcing them to display inappropriate ads, divert money from legitimate advertisements, and disguise themselves to avoid being crawled.
Because of this behavior he received the proper name of Agent Smith, one of the main (and most insistent) villains of the Matrix trilogy.
According to Check Point's analysis the malware originates in China (surprise surprise), specifically a security company based in Guangzhou, whose legitimate business (or facade in the case) is to help local developers distribute their apps to others markets. The devices would have been infected through a third-party shop called 9Apps, popular in Hindi, Arabic and Indonesian speaking countries, among other languages in the region.
The company says that Agent Smith has infected around 25 million Android devices silently, without the user realizing the attack thanks to its ability to conceal and conceal. About 15 million affected users are in India and nearby countries such as Pakistan and Bangladesh; however malware has been detected in at least 303,000 devices in the United States and 137,000 in the United Kingdom, and is also circulating in Australia.
The researchers also found evidence that malware developers attempted to infect the Google Play Store; code evidence from a previous version was found in at least 11 applications, but Google was able to remove all of those at risk and because of that, the malicious app could not propagate through the official store.
In fact, the plague takes advantage of a flaw called Janus corrected by Google when the introduction of Android 7.0 Nougat, but that depends on the developers of the apps to be implemented. It should be noted that 73.7% of the affected devices run 5.0 Lollipop and 6.0 Marshmallow versions (40.2% and 33.5% respectively), but 25.1% of the total are in the latest versions (15.8% with 7.0 and 8.3% with 8.0 Oreo). Apparently, a lot of people did not do their homework.
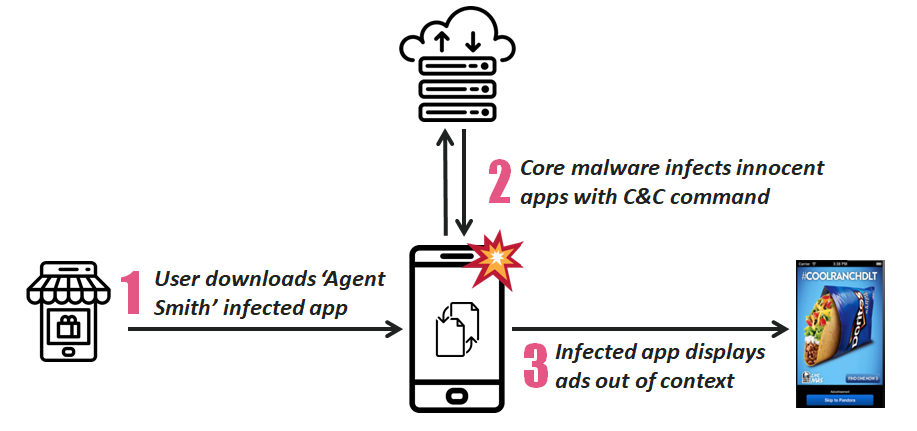
Once installed, Agent Smith scans the list of installed apps and finds a compatible one (for example, with processes with embedded or hard-coded code, which everyone knows is a bad practice, or sent by a C & C server) will extract the base .apk file, apply a malicious patch to the file, and replace the original with the infected one, as if it were an update. Among the most vulnerable applications are WhatsApp, Opera, MX Video Player and SwiftKey, among others.
Once infected, apps begin to display ads out of context and in large quantities, with money being rolled back to malware developers; Agent Smith variants are also capable of intercepting legitimate advertisements, replacing them with fraudulent ones, and rolling back money for themselves.
Check Point reports that while malware is currently being used for fast app and profit viewing, it may well be used for more harmful activities such as stealing personal data, bank passwords and credentials, turning the Android phone into a zombie, attached to a botnet and so on. Thanks to their ability to hide, the possibilities are endless.
The security company says it is working directly with Google; the search giant informs that Agent Smith has not been able to infiltrate the apps store and therefore, who does not usually install applications from outside is safe. No more worth the old rule: be careful what you install on your phone and if possible , avoid any type of software that is not distributed directly. Via: Check Point Research and Avast Blog

No comments:
Post a Comment