TECH
US scientists create anti-hacker processor
A new computer processor architecture developed at the University of Michigan promises nothing less than laying the groundwork for a future in which computers proactively defend against threats by making obsolete the current security model of finding bugs and releasing updates .
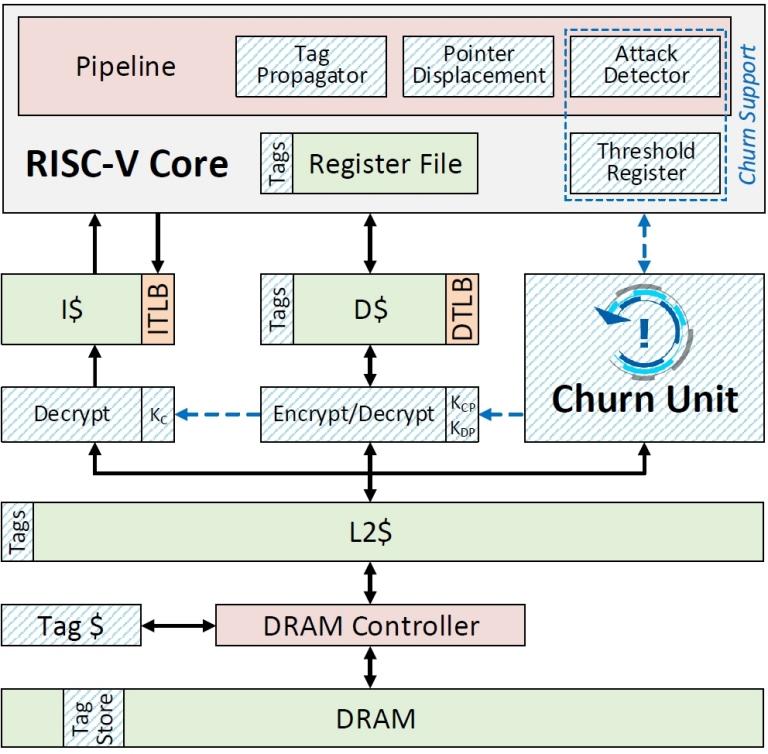
The new chip, dubbed Morpheus, blocks potential hacker attacks by randomly encrypting and rearranging key bits of its own code and its data 20 times per second.
This is infinitely faster than a human hacker can handle and thousands of times faster than the fastest electronic hacking techniques.
"The current approach of eliminating security errors one by one is a lost game.People are constantly writing code and as soon as there is a new code there will be new bugs and security vulnerabilities.With Morpheus, even if a hacker encounters a bug, the information needed to exploit it disappears 50 milliseconds later.It is perhaps the closest thing to a secure system proof of what will come in the future, "said Professor Todd Austin.
Agitation and indefinite semantics
Instead of using software to fix code vulnerabilities as they are discovered, the Morpheus processor includes security in its hardware. The constant randomization of critical program resources, in a process called "churn" (agitation or turnover), makes vulnerabilities virtually impossible to identify and exploit.
Still, data churn and its randomization by the processor are transparent to software developers and end users. This is because the mechanism is based on the randomization of data bits known as "indefinite semantics," which refers to the obscure nooks and crannies of the computing architecture - for example, the location, format, and content of a program's code is indefinite semantics .
The indefinite semantics is part of the most basic machinery of a processor. Legitimate programmers generally do not interact with it, but hackers can reverse-engineer vulnerabilities and initiate an attack.
The rate of "shaking" the chip can be adjusted up or down to find the right balance between maximizing security and minimizing resource consumption. Professor Austin says that the randomization rate of once every 50 milliseconds has been chosen for the demonstration processor because it is thousands of times faster than the faster electronic hacking techniques while reducing performance by only about 1% . The architecture also includes an attack detector that looks for pending threats and increases the rate of randomization if it realizes that an attack is imminent.
The demonstration chip is a RISC-V processor - a common, open-source chip design often used for research. The team is already trying to market the technology. Source: A Vulnerability-Tolerant Secure Architecture Based on Ensembles of Moving Target Defenses with Churn
Mark Gallagher, Lauren Biernacki, Shibo Chen, Zelalem Birhanu Aweke, Salessawi Ferede Yitbarek, Misato Tadesse Aga, Austin Harris, Zhixing Xu, Baris Kasikci, Valeria Bertacco, Sharad Malik, Mohit Tiwari, Todd Austin
Proceedings of the Twenty-Fourth International Conference on Architectural Support for Programming Languages and Operating Systems

No comments:
Post a Comment