DIGITAL LIFE
Hacked TP-Link routers at center of massive botnet used to attack Azure customers
CovertNetwork-1658 is a stark reminder of the ongoing cat-and-mouse game between cybersecurity professionals and threat actors. Using compromised devices as part of a botnet also underscores the importance of securing IoT devices and regularly updating firmware on routers and other network equipment.
Microsoft has exposed a complex network of compromised devices that Chinese hackers are using to launch highly evasive password spray attacks against Microsoft Azure customers. This network, dubbed CovertNetwork-1658 by Microsoft, has been actively stealing credentials from multiple Microsoft customers since August 2023.
The attacks use a botnet of thousands of small office and home office (SOHO) routers, cameras, and other Internet-connected devices. At its peak, there were more than 16,000 devices in the botnet, most of which were TP-Link routers.
CovertNetwork-1658, also known as xlogin and Quad7 (7777), is believed to be established and maintained by a threat actor located in China. The network's name stems from Microsoft's classification system, where "CovertNetwork" refers to a collection of egress IPs consisting of compromised or leased devices that may be used by one or more threat actors.
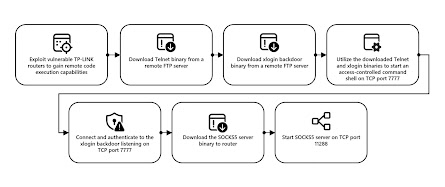
The hackers exploit a vulnerability in the routers to gain remote code execution capability, although the specific exploit method is still under investigation. Once access is achieved, the threat actors take several steps to prepare the router for password spray operations. These steps include downloading Telnet and xlogin backdoor binaries from a remote File Transfer Protocol (FTP) server, starting an access-controlled command shell on TCP port 7777, and setting up a SOCKS5 server on TCP port 11288.
CovertNetwork-1658 is highly evasive, making it particularly dangerous. The password spray attacks are conducted through this proxy network, ensuring that the attempts originate from the compromised devices. In about 80 percent of cases, CovertNetwork-1658 makes only one sign-in attempt per account daily, making it difficult to detect using traditional security measures.
The network also uses compromised SOHO IP addresses, a rotating set of IP addresses, and the low-volume password spray process. On average, Microsoft has observed about 8,000 compromised devices actively engaged in the CovertNetwork-1658 network at any given time, with approximately 20 percent of these devices performing password spraying.
Microsoft has linked the source of these password spray attacks to multiple Chinese threat actors. In particular, a group known as Storm-0940 has been observed using credentials obtained from CovertNetwork-1658. The relationship between CovertNetwork-1658 and Storm-0940 appears to be close, with Microsoft having observed Storm-0940 using compromised credentials obtained from CovertNetwork-1658 on the same day.
Once Storm-0940 gains access to a victim's environment, it uses various tactics to expand its reach. These include scanning and credential dumping tools for lateral movement within the network, attempting to access network devices and install proxy tools and remote access trojans (RATs) for persistence, and attempting to exfiltrate data.
The scale of this operation is particularly concerning, as any threat actor using the CovertNetwork-1658 infrastructure can conduct massive password-spraying campaigns. This, combined with the quick turnover of compromised credentials between CovertNetwork-1658 and Chinese threat actors, means accounts can be compromised quickly across multiple sectors and geographic regions.
While recent reports from security vendors like Sekoia and Team Cymru have led to a decline in the usage of CovertNetwork-1658's original infrastructure, Microsoft believes that the network is still operational and that threat actors are likely acquiring new infrastructure with modified fingerprints to evade detection.
Microsoft has directly notified targeted or compromised customers. While Redmond didn't provide specific advice on how users of TP-Link routers and other affected devices can prevent or detect infections, some experts suggest that periodically rebooting these devices may help disinfect them temporarily.
mundophone


No comments:
Post a Comment